I just got a notification about the SSLv3 POODLE Vulnerability and the suggested fix is to disable SSLv3 protocol from your server that supports SSLv3.
If you have your SSL certificate configured on you AWS Elastic Load Balancer, you can quickly apply this fix by logging into your AWS management console and click on your ELB under EC2 menu. ?The following 2 screenshots show how to?FIX SSLv3 POODLE vulnerability on your servers.

ELB?Edit Listeners
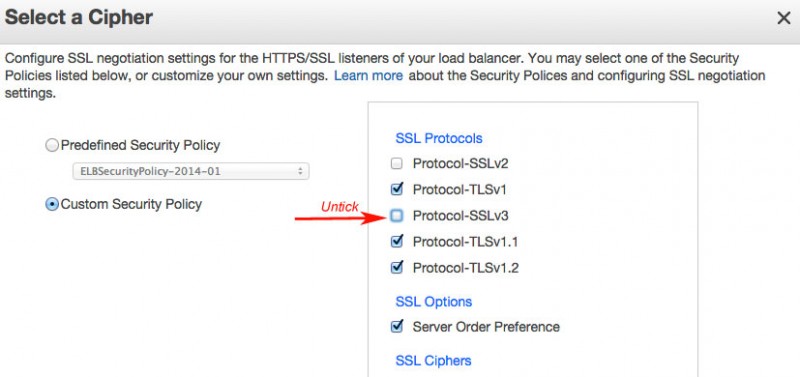
Then locate your security policy and untick the SSLv3 Protocol. If you security policy is one of AWS Predefined policies, you will need to tick the “Custom Security Policy” radio button to make the Protocols editable. ?See below:

AWS ELB SSL ciphers
If you have configured your SSL certificate on Nginx web server, make sure you remove the SSLv3 protocol by changing this:
ssl_protocols SSLv3 TLSv1 TLSv1.1 TLSv1.2;
to this:
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;
restart Nginx and this should FIX SSLv3 POODLE vulnerability.
More info on this issue can be found on the Ubuntu Forum.
Marko